Inside Cyber Warfare : Threat Actors, CISO Mistakes & Ransomware with TRUESEC’s Hasain Alshakarti
In the ever-escalating battleground of cybersecurity, theoretical knowledge is valuable, but real-world experience from the front lines is invaluable. We recently had the profound honor of hosting Hasain Alshakarti on the Sentinel Talk Show – a Principal Cybersecurity Advisor, Microsoft MVP, and a true veteran with over 30 years in security and infrastructure. His insights, drawn from countless incident responses, penetration tests, and strategic engagements, offer a candid look at the biggest threats and most common mistakes organizations are making today.
Inside the Cyber Trenches: Unpacking Real-World Security with Hasain Alshakarti
If you’re a CISO, a security engineer, or anyone striving to build resilient defenses, this episode (and this recap!) is a critical read. Here’s a deep dive into the powerful takeaways from our conversation with Hasain:
1. Unmasking the Adversary: What Threat Actors Are Really Doing
Hasain pulled back the curtain on the evolving tactics of cybercriminals and state-sponsored groups. He emphasized that threat actors are constantly refining their approaches, often leveraging stolen credentials, supply chain vulnerabilities, and social engineering to gain initial access. It’s not just about sophisticated zero-days; often, it’s about exploiting fundamental weaknesses in an organization’s security posture. Understanding their Tactics, Techniques, and Procedures (TTPs), rather than just indicators of compromise (IOCs), is crucial for proactive defense.
2. CISO Blind Spots: The Mistakes Organizations Keep Making
One of the most sobering parts of our discussion was Hasain’s blunt assessment of common CISO and leadership errors. He highlighted how many organizations:
- Underestimate the Basics: Overlooking foundational security hygiene like patching, strong access controls, and proper configuration management in favor of shiny new tools.
- Lack of Prioritization: Failing to identify and focus on the most critical assets and the threats that pose the greatest risk to the business.
- Poor Incident Response Planning: Not having a well-tested, up-to-date incident response plan, leading to chaos and prolonged recovery during an actual breach.
- Insufficient Investment in People: Neglecting to adequately train and retain skilled security professionals.
- A “Set It and Forget It” Mentality: Assuming security solutions, once implemented, don’t require continuous monitoring, tuning, and adaptation.
3. Top Issues from the Trenches: Where to Focus Your Efforts NOW
Based on his extensive engagements, Hasain pinpointed the most prevalent and impactful issues he encounters:
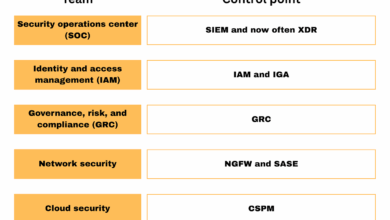
- Identity and Access Management (IAM): Weaknesses in identity lifecycle management, multi-factor authentication (MFA) bypasses, and excessive privileges remain prime targets.
- Vulnerability Management: Inadequate patching cycles and failure to address known critical vulnerabilities consistently.
- Supply Chain Risk: The increasing threat posed by vulnerabilities within third-party software and services.
- Logging and Monitoring: Insufficient logging or lack of effective Security Information and Event Management (SIEM) that prevents timely detection of intrusions.
4. Ransomware: The Ever-Present Scourge
The conversation naturally turned to ransomware, a threat that continues to evolve and devastate businesses. Hasain discussed the shift towards “double extortion,” where data is not only encrypted but also exfiltrated and threatened with public release. His key advice for ransomware defense revolved around:
- Robust Backups & Recovery: Immutable, offline backups are non-negotiable.
- Network Segmentation: Limiting lateral movement for attackers.
- Strong Endpoint Detection & Response (EDR): Powerful tools to detect and block malicious activity.
- User Training: Educating employees about phishing and social engineering tactics often used to deliver ransomware.
5. GRC: Beyond Compliance – Truly Reducing Risk
Governance, Risk, and Compliance (GRC) often gets a bad rap for being overly bureaucratic. Hasain emphasized that effective GRC isn’t just about checking boxes; it’s about genuinely reducing risk and providing tangible value. The focus should be on understanding the actual risks to the business and aligning security controls to mitigate them, rather than just meeting minimum regulatory requirements. GRC should be a framework for continuous improvement, driven by a deep understanding of the threat landscape and business objectives.
Final Thoughts from the Master
Hasain Alshakarti’s insights serve as a powerful wake-up call and a practical guide. In an environment where threats are constantly adapting, our defenses must be equally dynamic. It’s about getting the fundamentals right, understanding the adversary, being prepared for the inevitable, and fostering a culture of continuous security improvement.
Did you catch this essential episode? If not, you can watch the full conversation with Hasain Alshakarti
What was your biggest takeaway from Hasain’s insights? Or what’s the most critical cybersecurity challenge your organization is facing right now? Share your thoughts in the comments below!
You can watch the other episodes of Sentinel Talk show here
YouTube : https://lnkd.in/esqiXrXV
Spotify : https://lnkd.in/eWPQkyjc


Evolution of Ransomware and Proactive Cybersecurity Strategies
Automated DFIR Rethinking the SOC
Navigating 2025 Cyber Frontier with Lyfts CISO
Recent Cyberattacks Highlight Network Vulnerabilities – Free Webinar
Empowering You to Make the Right Choice: A Guide to Endpoint Protection
India vs Pakistan Cyber Conflict – Decoding the Digital Battlefield
Legal and Regulatory Landscape of Endpoint Security
Keywords
Inside Cyber Warfare : Threat Actors, CISO Mistakes & Ransomware ransomware and cyber extortion cyber attack vectors the cyber threat outlook common cyber attack attack vectors securing your environment endpoint detection and response edr cybersecurity and credit union