-
UNIQAL

LA Fires : Picking Up the Pieces and How to Rebuild Your Life
Tragedy often strikes when you least expect it. Many of my clients, as well as myself, have faced the devastating…
Read More » -
CAPLEX

Neural Hijacking: Is Your Brain Making Security Decisions Without You?
Introduction: The Battlefield Inside Your Head In cybersecurity, we master firewalls and encryption. But are we neglecting the most critical…
Read More » -
CAPTIX

Welcome Our Newest Associate Participating Organizations
We are pleased to welcome the newest organizations that have joined as Associate Participating Organizations of the PCI Security…
Read More » -
CAPTOL
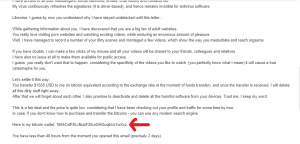
Don’t Be a Victim! Blackmail Scam Emails Exposed
Sextortion scam emails have become a disturbingly common occurrence in people’s inboxes. These menacing messages claim the sender has hacked…
Read More » -
CAPTUR

The Immanence of the Useless. It is good that is not any good | by Vicente Aceituno Canal | Assorted Thoughts
It is good that is not any good Zoom image will be displayed Photo by Madalyn Cox on Unsplash “Perfection…
Read More » -
CAPVEX

Using 2nd Sight Lab’s aws-deploy to Deploy Any AWS Resource | by Teri Radichel | Cloud Security | Jul, 2025
Steps to deploy all the things — and summary of how I used AI ~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~ ⚙️ Security Automation (Pre-AI). The…
Read More » -
UNIQAL

Understanding Your Health Insurance Policy: A Guide for Business Owners
As a business owner, you already wear many hats. From managing daily operations to leading your team, your responsibilities are…
Read More » -
CAPLEX

How OAuth and device code flows get abused
Microsoft Entra ID, the identity backbone of Microsoft’s cloud ecosystem, is increasingly targeted through techniques like Device Code Phishing and…
Read More » -
CAPTIX

How Smart MSPs Sell with Compliance, Not Just Tools
Today we’re digging into one of the most dreaded but potentially most powerful parts of running an MSP compliance. For…
Read More » -
CAPTOL

AI-enabled phishing attacks on consumers: How to detect and protect
Phishing attacks are a significant threat to consumers, with cybercriminals constantly evolving their tactics to deceive unsuspecting individuals. The integration…
Read More »