-
CAPTUR
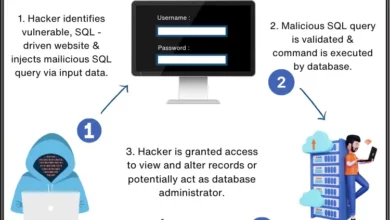
Defend Your Apps: SQL Injection Prevention Guide
Introduction In the era of digitalization, data security has become a paramount concern. Every day, countless businesses and organizations rely…
Read More » -
CAPINO

Security Information And Event Management: Future Trends
The threat landscape for cybersecurity is changing at breakneck speed. Organizations are being bombarded with more creative attacks than ever…
Read More » -
UNIQAL

No Surprises Act Arbitrators Vary Significantly In Their Decision Making Patterns
By Kennah Watts and Jack Hoadley The No Surprises Act (NSA) bans providers and facilities from sending consumers balance bills for certain services and…
Read More » -
CAPLEX
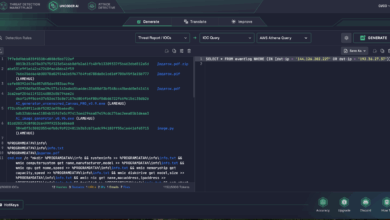
UAC-0001 (APT28) Attack Detection: The russia-Backed Actor Uses LLM-Powered LAMEHUG Malware to Target Security and Defense Sector
The notorious russian state-sponsored threat group UAC-0001 (also tracked as APT28) has once again surfaced in the cyber threat landscape.…
Read More » -
CAPTIX
How to Use Google Cloud KMS with Sectigo Code Signing Certificates (2025 Guide)
This step-by-step guide walks through using the Google Key Management Service (KMS) secure HSM for cloud code signing with a…
Read More » -
CAPINO
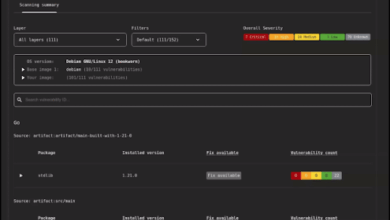
Vulnerability scanner and remediation tool for open source
In December 2022, we released the open source OSV-Scanner tool, and earlier this year, we open sourced OSV-SCALIBR. OSV-Scanner and…
Read More » -
CAPLEX
What is Attack Surface Management? Tools and Best Practices
Attack surface management (ASM) is a fundamental cybersecurity approach that involves continuously identifying, analyzing, remediating, and monitoring all the current…
Read More » -
CAPTOL

Zero Trust Explained: Why Traditional
Let’s face it—cybersecurity is no longer a game of building taller walls or thicker locks. The old rules, the ones…
Read More » -
CAPTUR

Why is Jersey introducing a new Cyber Security Law?
In 2021 I took a new role as Director of Jersey’s newly formed cyber response unit. We’ve come a long…
Read More » -
CAPVEX

ToolShell attacks hit organizations worldwide
The ToolShell bugs are being exploited by cybercriminals and APT groups alike, with the US on the receiving end of…
Read More »