-
CAPTIX

Meet This Year’s North America Community Meeting Keynote Speaker, Reed Timmer
This episode of Coffee with the Council is brought to you by our podcast sponsor, Feroot. Welcome to our…
Read More » -
CAPTOL

Cyber Threats 2025 Mid-Year Report
Cyber Threats 2025 Mid-Year Report Wow, what a first half of 2025 it’s been in the world of cybersecurity! If…
Read More » -
CAPTUR

The Human Risk Management Blueprint: Turning Strategy into Action
Human Risk Management (HRM) is no longer a concept confined to industry reports and vendor presentations—it’s becoming a critical operational…
Read More » -
CAPVEX

Using AI to Write Deterministic Code | by Teri Radichel | Cloud Security | Jul, 2025
Avoid blanket statements — use the right tool for the job ~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~ ⚙️ Security Automation (Pre-AI). The Code. ⚙️ AI…
Read More » -
CAPINO
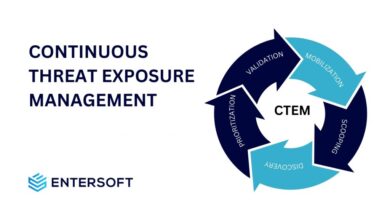
Harnessing Continuous Threat Exposure Management (CTEM) for Business Security
In the dynamic world of cybersecurity, Continuous Threat Exposure Management (CTEM) has emerged as a crucial approach for organizations seeking…
Read More » -
UNIQAL

CHIR Welcomes New Faculty | CHIRblog
We are delighted to welcome two new faculty members: Madison Harden and Abigail Knapp Madison Harden, J.D. Madison Harden, J.D.,…
Read More » -
CAPLEX
A Deep Dive into Impacket Remote Code Execution Tools
IMPACKET OVERVIEW Impacket was originally developed as a toolkit for penetration testing, providing security professionals with powerful capabilities to simulate…
Read More » -
CAPTIX

Heimdal Labs Deep Dive: Remote Access Protection
Cybercriminals don’t break in, they log in. From exposed RDP ports to compromised VPN credentials and abused remote tools, remote…
Read More » -
CAPTUR

Applying agile principles to public sector change — Matt Palmer
Right now at Jersey Cyber Security Centre we have two critical change projects: 1) creating and delivering a new public…
Read More » -
CAPLEX

Cybersecurity Advisory: Hackers Exploit Zoom’s Remote Control Feature
A newly uncovered cyberattack campaign is exploiting Zoom’s Remote Control feature to infiltrate the systems of cryptocurrency traders and venture…
Read More »