-
CAPTOL

How to Avoid Telehealth Security and Privacy Risks
Editor’s note: Alena describes the most effective measures to ensure security for a telehealth application. And if you consider creating a…
Read More » -
CAPTUR
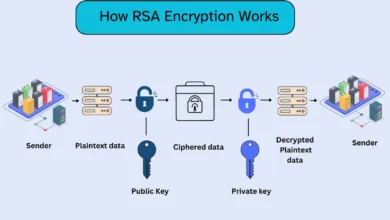
Enduring Power of RSA Encryption in Securing Network Communications
Introduction As organizations and individuals rely increasingly on digital systems to communicate and share sensitive information online, robust encryption methods…
Read More » -
CAPVEX

Unlocking Cybersecurity Success: Navigating Careers with Certifications
Navigating a Successful Career Transition in Cybersecurity: The Crucial Role of Certifications In the fast-paced and competitive field of cybersecurity,…
Read More » -
CAPINO
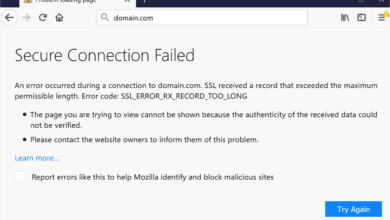
Fix SSL_ERROR_RX_RECORD_TOO_LONG in Firefox – Quick Guide
When Firefox throws up the error SSL_ERROR_RX_RECORD_TOO_LONG, it’s not just a random glitch. It’s Firefox’s way of protecting you when…
Read More » -
UNIQAL

Stay Healthy with Free Preventative Care: What You Need to Know
Although it might take some time to set up your free preventative exam with your in-network doctor, it is well…
Read More » -
CAPLEX

CyberHoot Newsletter – May 2025
Welcome to CyberHoot’s May Newsletter! This month, we’re spotlighting key developments in the cyber threat landscape, including a malvertising phishing…
Read More » -
CAPTIX

The 4 CISM Domains Explained
The CISM® (Certified Information Security Manager®) qualification from ISACA® is one of the most widely respected credentials for information security…
Read More » -
CAPTOL
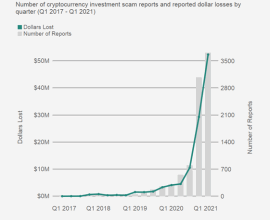
Strategies to overcome the cryptocurrency scam
Cryptocurrency has revolutionized financial transactions, offering speed, anonymity, and decentralization. However, the rise of cryptoscams has become a significant concern…
Read More » -
CAPTUR

A Cybermaniac’s Commentary on the Human Factor in Ransomware 2025
Insight from our CEO of Cybermaniacs – here’s what I’d say to a boardroom full of CISOs and execs reading…
Read More » -
CAPVEX

How to handle and spot phishing mails with Microsoft Defender
In the previous blog post, we went through how Microsoft Defender can strengthen your email security. If you haven’t read…
Read More »