-
CAPLEX

Your Protection Guide for Cybersecurity in Retail and Ecommerce
It’s surely the biggest fear of any e-commerce site manager. You try logging into your CRM, CMS or inventory management…
Read More » -
CAPTIX

Your Protection Guide For Cybersecurity in Manufacturing
Cybersecurity in manufacturing businesses is unique. The sector faces several challenges that other industries don’t have to contend with. And…
Read More » -
CAPTUR

A Journey to the Highest Cybersecurity Maturity: Performance, Part 9
Activity Management Continue reading on The CISO Den »
Read More » -
CAPVEX

Why the tech industry needs to stand firm on preserving end-to-end encryption
Restricting end-to-end encryption on a single-country basis would not only be absurdly difficult to enforce, but it would also fail…
Read More » -
CAPINO
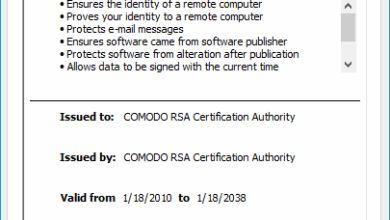
Comodo RSA Certification Authority: Trusted Root CA Explained
The COMODO RSA Certification Authority is one of the most widely distributed root CAs in the world. Its certificates form…
Read More » -
CAPLEX

Are Creatives Fleeing Instagram Due to AI?
Meta admitted last month that it was using content posted to its flagship platforms Facebook and Instagram to train its…
Read More » -
CAPTIX
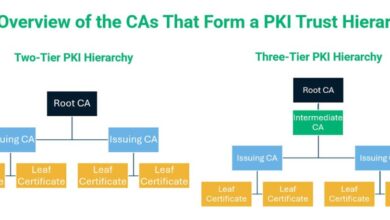
Demystifying PKI Technology: An Essential Guide for IT Security Professionals
Learn everything you need to know about PKI technology in IT security that enables organizations to establish trust in a…
Read More » -
CAPTOL
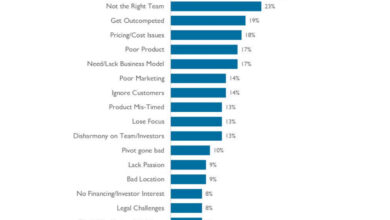
Cybersecurity is changing how financial markets work but not in the way people think
People like to say that public markets don’t really care about security and that the impact of security incidents on…
Read More » -
CAPTUR
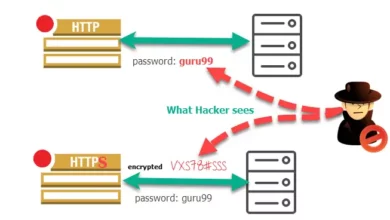
SSL Pinning Bypass with Frida and effective Mitigation techniques
Introduction In an era of unprecedented digital transformation, securing sensitive data and communications has never been more critical. One of…
Read More » -
CAPINO

The Role of EDR in Real-Time Threat Detection & Response
Understanding how EDRs work requires examining the sophisticated mechanisms that enable these systems to detect, analyze, and respond to cybersecurity…
Read More »