-
CAPLEX
Interlock Ransomware Detection: Adversaries Deploy a Novel PHP-Based RAT Variant via FileFix
Threat actors operating the Interlock ransomware, known for executing high-impact double-extortion attacks across various global industries, have re-emerged in the…
Read More » -
CAPTIX

Cybersecurity in Education – Definition, Threats, Stats and Solutions
With 217 ransomware attacks hitting educational organizations in the past year alone (a 35% increase), the message is clear: educational…
Read More » -
CAPTOL

Smishing Scams Are on the Rise: How to Spot and
Text messages used to be a safe space—quick birthday wishes, delivery updates, maybe the odd emoji from a friend. But…
Read More » -
CAPTUR

Not Every Task Deserves One
Hello CyberBuilders 🖖 This week, I’m diving into a brilliant video from Mr. Zhang at Anthropic. You might know him…
Read More » -
CAPVEX

Amazon Q For Code to Deploy a User and Secret With Password | by Teri Radichel | Cloud Security | Jun, 2025
WARNING: Do not blindly create IAM resources with AI ~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~ ⚙️ Security Automation (Pre-AI). The Code. ⚙️ AI Automation. The…
Read More » -
UNIQAL

Building a Strong Company Culture Through Employee Benefits
As a business owner in Arizona, you already know that your employees are your greatest asset. Their hard work, creativity,…
Read More » -
CAPLEX
NIST 800-53 Compliance Checklist and Security Controls Guide
Ensuring compliance with NIST SP 800-53 is critical for aligning your cybersecurity efforts with federal standards. This popular cybersecurity framework…
Read More » -
CAPTIX
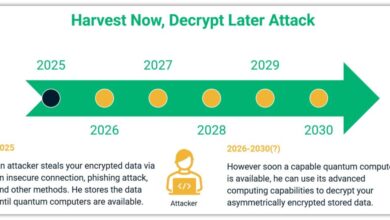
What ‘Harvest Now, Decrypt Later’ Means for SMBs (and 7 Steps to Prevent These Attacks)
Quantum computing doesn’t mean the end of the world, but its eventual arrival will threaten the security of your data.…
Read More » -
CAPTOL

How to Shop Safely During Amazon Prime Day
As Amazon Prime Day approaches (July 8-11, 2025), millions of shoppers are gearing up for what promises to be one…
Read More » -
CAPTUR

A Journey to the Highest Cybersecurity Maturity: Remediation, Part 5
Remediation Cycle Continue reading on The CISO Den »
Read More »