CAPINO
-
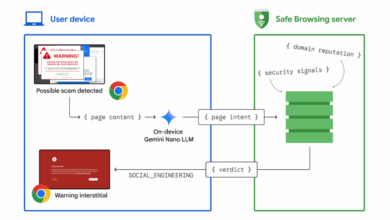
Using AI to stop tech support scams in Chrome
Posted by Jasika Bawa, Andy Lim, and Xinghui Lu, Google Chrome Security Tech support scams are an increasingly prevalent form…
Read More » -
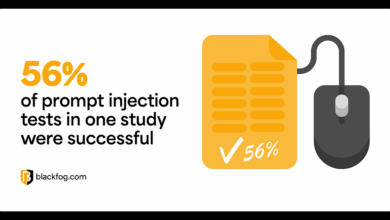
How Can a Zero-Trust Approach Help Guard Against LLM prompt injection attacks?
How Can a Zero-Trust Approach Help Guard Against LLM Prompt Injection Attacks? As artificial intelligence becomes more embedded in business…
Read More » -

Top 6 VAPT Tools for 2024 You Should Know
IntroductionCybersecurity threats continue to evolve, making Vulnerability Assessment and Penetration Testing (VAPT) an essential practice for organizations. In this blog,…
Read More » -
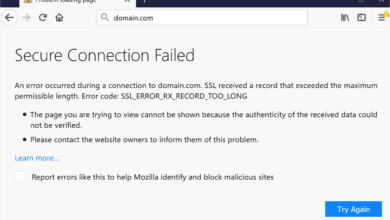
Fix SSL_ERROR_RX_RECORD_TOO_LONG in Firefox – Quick Guide
When Firefox throws up the error SSL_ERROR_RX_RECORD_TOO_LONG, it’s not just a random glitch. It’s Firefox’s way of protecting you when…
Read More » -

EDR Meaning in Cybersecurity: Key Trends and Innovations
The cybersecurity field continues to expand with new acronyms and technologies appearing regularly. Among these, EDR has become one of…
Read More » -
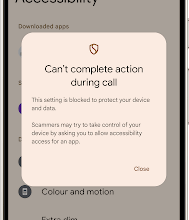
What’s New in Android Security and Privacy in 2025
Posted by Dave Kleidermacher, VP Engineering, Android Security and Privacy Android’s intelligent protections keep you safe from everyday dangers. Our…
Read More » -
LLM Cybersecurity: How Businesses Can Protect and Leverage AI Safely
LLM Cybersecurity: How Businesses Can Protect and Leverage AI Safely The rapid rise of artificial intelligence in business has brought…
Read More » -
What is API Security Testing: Complete Guide
Introduction APIs are essential for modern software, enabling communication between applications, services, and devices. However, with increased use, APIs also…
Read More » -
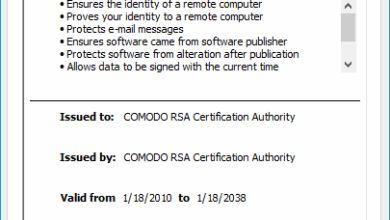
Comodo RSA Certification Authority: Trusted Root CA Explained
The COMODO RSA Certification Authority is one of the most widely distributed root CAs in the world. Its certificates form…
Read More » -

The Role of EDR in Real-Time Threat Detection & Response
Understanding how EDRs work requires examining the sophisticated mechanisms that enable these systems to detect, analyze, and respond to cybersecurity…
Read More »