CAPINO
-
Google’s Strongest Security for Mobile Devices
Posted by Il-Sung Lee, Group Product Manager, Android Security Protecting users who need heightened security has been a long-standing commitment…
Read More » -

Prompt Injection Attacks: Types, Risks and Prevention
Prompt Injection Attacks: Types, Risks and Prevention It’s no longer news that AI is changing how many businesses think. In…
Read More » -

Black-Box vs White-Box Penetration Testing Explained
Introduction When securing your applications, choosing the right penetration testing methodology is crucial. Two widely used techniques are Black-Box Testing…
Read More » -
SSL/TLS Certificate Lifetimes Drop to 47 Days by 2029
In April 2025, the CA/Browser Forum, with support from Apple, Google, and Mozilla, approved a proposal to shorten the maximum…
Read More » -

Best Solutions for Cyber Defense
The cybersecurity market continues to grow as organizations face increasingly sophisticated threats that require advanced monitoring and response capabilities. Security…
Read More » -
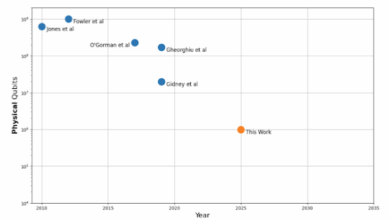
Tracking the Cost of Quantum Factoring
Google Quantum AI’s mission is to build best in class quantum computing for otherwise unsolvable problems. For decades the quantum…
Read More » -

Adaptive Security: Why Cyber Defense Needs to Evolve with the Threat Landscape
Adaptive Security: Why Cyber Defense Needs to Evolve with the Threat Landscape The growing adoption of technologies like AI, automation…
Read More » -

#What is Cloud Security Testing for Multi-Cloud
Introduction As businesses increasingly adopt multi-cloud environments for greater flexibility, they also face unique security challenges. Each cloud provider has…
Read More » -

Critical: Raspberry Robin Deploys CLFS Exploit to Escalate Privileges on Windows
Executive Summary The Raspberry Robin malware, a sophisticated and evolving threat, actively exploits a new vulnerability in Windows systems. First…
Read More » -
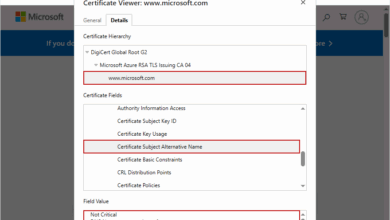
What is a SAN SSL Certificate?
If an organization handles multiple number of domains, subdomains, or internal services, it is likely to become inefficient or error-prone.…
Read More »