CAPLEX
-

Cybersecurity’s Blind Spot: Why Human Behavior is Every CISO’s Business
When a major breach makes headlines, the impact ripples far beyond the individuals whose data has been compromised. It shakes…
Read More » -
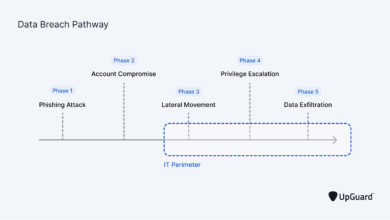
How to Prevent Data Breaches in 2025 (Highly Effective Strategy)
A data breach occurs when sensitive information is exposed to the public without authorization. These events are growing in popularity,…
Read More » -

The Seven Digital Sins
It’s no secret the internet doesn’t always bring out the best in people. The relative anonymity and global sprawl of…
Read More » -

How To Secure Your Computer Against Cyber Threats Like 007
Want to secure your computer against cyber threats? Are you aware of the latest cyber threats? This post is meant…
Read More » -

Legacy Solutions Have Become a Cyber Defense Problem
The cyber defense community is at a crossroads that is magnified by cyber criminals’ adoption of AI and ransomware-as-a-service. With…
Read More » -
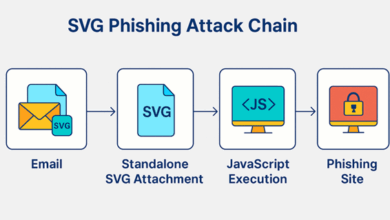
How Hackers Use Vector Graphics for Phishing Attacks
Introduction In the ever-evolving cybersecurity landscape, attackers constantly seek new ways to bypass traditional defences. One of the latest and…
Read More » -
Tarah Wheeler Narrowly Avoids Getting Got
No one is immune from being scammed. Just ask Tarah Wheeler, founder and CEO of Red Queen Dynamics, a company…
Read More » -

Mind the Middle – Cyber Defense Magazine
In an era where digital threats can cripple a business overnight, where threat actors can use AI to customize and…
Read More » -

Webinar on demand: The ROI of SOC
Join cybersecurity leaders from G’Secure Labs and Logpoint as they break down what truly defines SOC success. Discover how…
Read More » -

Ingram Micro Ransomware Attack Shakes IT Supply Chain
Your weekly dose of the most urgent cyber threats is here. Adam Pilton distilled it all into five critical stories…
Read More »