CAPLEX
-

Carina Follows Her Heart Into a Crypto Scam
No one’s too smart for a well-designed scam. Case in point, neuroscientist, triathlete Carina who thought the finance bro she…
Read More » -

8 Popular Types Of Cybercrimes In The 21st Century
Looking for a detailed list of the most popular types of cybercrimes in today’s digital world? Read on. In this…
Read More » -
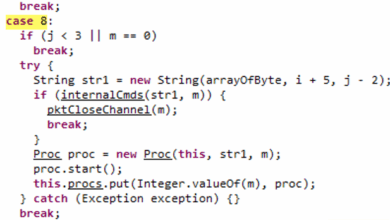
Cleo MFT Mass Exploitation Payload Analysis
1. Cli Class Purpose: Orchestrates the execution of commands, manages the lifecycle of the payload, and interacts with the server…
Read More » -

Multifaceted Cyber-Attacks Require a Unified Defense Approach
Gone are the days of attacks hitting a single product or vulnerability. Today, we’re seeing the increasing use of multi-vector…
Read More » -

Webinar: Elevate your security with Microsoft Defender XDR Integration
21 May 2025, 10:00 – 11:00 CET We’re excited to invite you to an exclusive webinar, where we introduce…
Read More » -
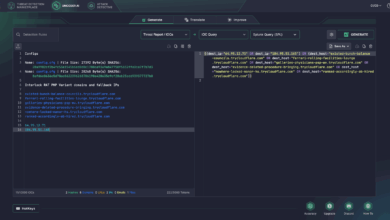
Interlock Ransomware Detection: Adversaries Deploy a Novel PHP-Based RAT Variant via FileFix
Threat actors operating the Interlock ransomware, known for executing high-impact double-extortion attacks across various global industries, have re-emerged in the…
Read More » -
NIST 800-53 Compliance Checklist and Security Controls Guide
Ensuring compliance with NIST SP 800-53 is critical for aligning your cybersecurity efforts with federal standards. This popular cybersecurity framework…
Read More » -

Heimdal Achieves IP Co-Sell Ready and MACC Eligible Status with Microsoft
Heimdal can now be purchased through Microsoft’s global sales teams and counts toward Azure spending commitments. This partnership opens new…
Read More » -

Becky Holmes Knows Who *Isn’t* Dating Keanu Reeves
Becky Holmes loves DMing with scammers. When it comes to romance scammers, she will do whatever it takes, pursuing them…
Read More » -

Do I Need Antivirus App On Android Phone?
Do I need antivirus app on Android phone? Read on for the answer. Antivirus apps are known to provide extra…
Read More »