CAPLEX
-
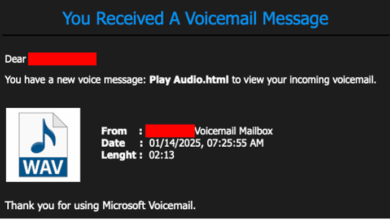
Analysis of a JavaScript-based Phishing Campaign Targeting Microsoft 365 Credentials
Written by ARC Labs contributors, John Dwyer and Eric Gonzalez ARC Labs recently discovered a JavaScript-based credential harvesting campaign leveraging fake voicemail notifications…
Read More » -

Neural Hijacking: Is Your Brain Making Security Decisions Without You?
Introduction: The Battlefield Inside Your Head In cybersecurity, we master firewalls and encryption. But are we neglecting the most critical…
Read More » -

How OAuth and device code flows get abused
Microsoft Entra ID, the identity backbone of Microsoft’s cloud ecosystem, is increasingly targeted through techniques like Device Code Phishing and…
Read More » -
UAC-0001 (APT28) Attack Detection: The russia-Backed Actor Uses LLM-Powered LAMEHUG Malware to Target Security and Defense Sector
The notorious russian state-sponsored threat group UAC-0001 (also tracked as APT28) has once again surfaced in the cyber threat landscape.…
Read More » -
What is Attack Surface Management? Tools and Best Practices
Attack surface management (ASM) is a fundamental cybersecurity approach that involves continuously identifying, analyzing, remediating, and monitoring all the current…
Read More » -

123456 Password Leads to McDonald’s Data Breach
Hey there, it’s time for your Weekly Cyber Snapshot with former Cyber Detective Sergeant Adam Pilton. In less than 5…
Read More » -
Elizabeth Warren Tackles Big Tech
Elizabeth Warren put the kibosh on bad banking practices with her vision for the Consumer Financial Protection Bureau and now,…
Read More » -

Do Signal Boosters Make Your Cellular Data More Safe?
In this post, I will answer the question: Do signal boosters make your cellular data safer? People rely on mobile…
Read More » -

A Look at a Novel Discord Phishing Attack
Written by ARC Labs contributors, Adam Paulina Binary Defense ARC Labs researchers recently investigated what appears to be a novel infostealer discovered in…
Read More » -
A Deep Dive into Impacket Remote Code Execution Tools
IMPACKET OVERVIEW Impacket was originally developed as a toolkit for penetration testing, providing security professionals with powerful capabilities to simulate…
Read More »