CAPLEX
-

Cybersecurity Advisory: Hackers Exploit Zoom’s Remote Control Feature
A newly uncovered cyberattack campaign is exploiting Zoom’s Remote Control feature to infiltrate the systems of cryptocurrency traders and venture…
Read More » -
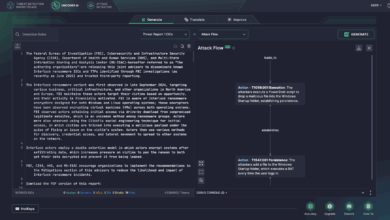
Interlock Ransomware Detection: The FBI, CISA, and Partners Issue Joint Alert on Massive Attacks via the ClickFix Social Engineering Technique
In mid-July 2025, researchers spread the news of the reemergence of the Interlock ransomware group, leveraging a modified version of…
Read More » -
Analyzing llama.cpp Servers for Prompt Leaks
The proliferation of AI has rapidly introduced many new software technologies, each with its own potential misconfigurations that can compromise…
Read More » -

The MSP Who Paid His Client’s Ransom and Tripled His Business
Most MSPs will tell you their worst nightmare is getting a call that a client has been breached. Dan Di…
Read More » -

Beth Should Have Dated the IT Guy
Beth sent more than $26,000 to a man she met on Tinder. It was a romance scam, but one that…
Read More » -

Banana Pro: The Fastest Way to Trade Meme Coins, Earn Auto Rewards, and Stay Ahead in Crypto
Banana Pro: The Fastest Way to Trade Meme Coins, Earn Auto Rewards, and Stay Ahead in Crypto Banana Gun just…
Read More » -
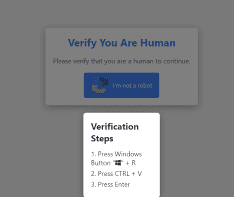
Analyzing LummaStealer’s FakeCAPTCHA Delivery Tactics
Written by ARC Labs contributor, Shannon Mong Threat actors continue to evolve their initial access tactics, blending social engineering with lightweight payload delivery…
Read More » -

Effortless Cloud Security: A Beginner’s Checklist for a Safer Cloud Environment
In the past few years, the world has embraced a new era of AI, introducing an array of security tools…
Read More » -
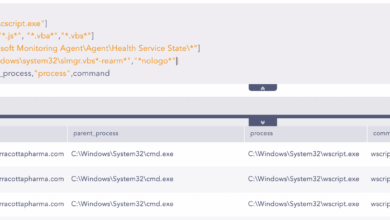
Pinpointing GRU’s TTPs in the Recent Campaign
Introduction Russia’s GRU Unit 26165, also known by several aliases, including APT28, is a name synonymous with cyber espionage, having…
Read More » -

CyberHoot Newsletter – May 2025
Welcome to CyberHoot’s May Newsletter! This month, we’re spotlighting key developments in the cyber threat landscape, including a malvertising phishing…
Read More »