CAPLEX
-
Koske Malware Detection: New AI-Generated Linux Threat in the Wild
Attackers are increasingly leveraging AI to compromise critical business assets, signaling a dangerous evolution in the threat landscape. Check Point…
Read More » -
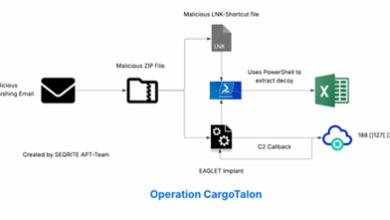
Ung0901 Targets Russian Aerospace Defense Using Eaglet Implant
Contents Introduction Initial Findings Infection Chain. Technical Analysis Stage 0 – Malicious Email File. Stage 1 – Malicious LNK file.…
Read More » -
Using Exposed Ollama APIs to Find DeepSeek Models
The explosion of AI has led to the creation of tools that make it more accessible, leading to more adoption…
Read More » -

Microsoft SharePoint Zero-Day Disrupts Servers Worldwide
Hey, it’s that time of week again. Cybersecurity Advisor Adam Pilton rips through the five biggest cyber headlines shaking up…
Read More » -

What to Expect in 2025
2024 is coming to a close, and with it a banner year for cybercrime. Megabreaches that would have grabbed front-page…
Read More » -

20 Best Cybersecurity Business Ideas For Entrepreneurs
Are you looking for the best cybersecurity business ideas? We have got you covered. Read on! Over half a million…
Read More » -
What CVE-2025-53770 Teaches Us About Zero-Day Reality and Ransomware Routine
CVE-2025-53770 is a critical SharePoint RCE flaw. It leverages unsafe deserialization and, when combined with one of several auth bypasses…
Read More » -
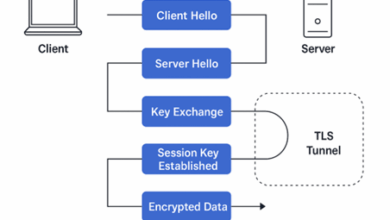
Post Quantum Threats – The Encryption Apocalypse That Isn’t
Preface RSA Conference just wrapped up, and while phrases like “We are an Agentic AI solution for XYZ,” “AI in…
Read More » -

APT28’s New Arsenal: LAMEHUG, the First AI-Powered Malware
Over the past few years, we’ve all been aware of the devastating war that has unfolded between Russia and Ukraine,…
Read More » -
CyberHoot Newsletter – June 2025
CyberHoot June Newsletter: Stay Informed, Stay Secure Welcome to the June edition of CyberHoot’s newsletter, where we keep you up…
Read More »