CAPTIX
-

Cybersecurity in Education – Definition, Threats, Stats and Solutions
With 217 ransomware attacks hitting educational organizations in the past year alone (a 35% increase), the message is clear: educational…
Read More » -
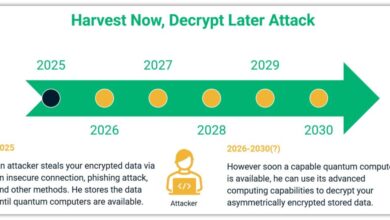
What ‘Harvest Now, Decrypt Later’ Means for SMBs (and 7 Steps to Prevent These Attacks)
Quantum computing doesn’t mean the end of the world, but its eventual arrival will threaten the security of your data.…
Read More » -

ISO 27001 Risk Assessment: 7 Step Guide
Risk assessments remain central to ISO 27001 compliance in 2025, ensuring your ISMS (information security management system) is robust and…
Read More » -

Preventing Zero-Click AI Threats: Insights from EchoLeak
EchoLeak (CVE-2025-32711) is a recently discovered vulnerability in Microsoft 365 Copilot, made more nefarious by its zero-click nature, meaning it…
Read More » -

Welcome Our Newest Associate Participating Organizations
We are pleased to welcome the newest organizations that have joined as Associate Participating Organizations of the PCI Security…
Read More » -

How Smart MSPs Sell with Compliance, Not Just Tools
Today we’re digging into one of the most dreaded but potentially most powerful parts of running an MSP compliance. For…
Read More » -
How to Use Google Cloud KMS with Sectigo Code Signing Certificates (2025 Guide)
This step-by-step guide walks through using the Google Key Management Service (KMS) secure HSM for cloud code signing with a…
Read More » -

The 5 CISA Domains Explained
The CISA® (Certified Information Systems Auditor®) credential, awarded by ISACA®, is the gold standard for IT audit, control and assurance…
Read More » -

CISA’s NIMBUS 2000 Initiative: Key Findings
How Trend Vision One™ Cloud Security Aligns with NIMBUS 2000 As a committed partner in the cloud security ecosystem, Trend Vision…
Read More » -

Meet This Year’s North America Community Meeting Keynote Speaker, Reed Timmer
This episode of Coffee with the Council is brought to you by our podcast sponsor, Feroot. Welcome to our…
Read More »