CAPTIX
-

Heimdal Labs Deep Dive: Remote Access Protection
Cybercriminals don’t break in, they log in. From exposed RDP ports to compromised VPN credentials and abused remote tools, remote…
Read More » -
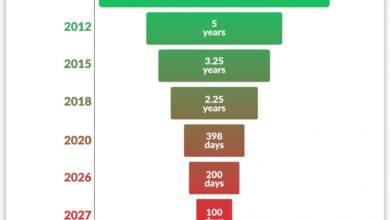
Industry Leaders Approve the Move to a 47-Day SSL Certificate Validity Period
By 2029, SSL/TLS certificates will be valid for a maximum of 1.5 months. Here’s what to know about the certificate…
Read More » -

Information Security vs Cyber Security: The Difference
You’ll often see the terms cyber security and information security used interchangeably. That’s because, in their most basic forms, they have the same aim:…
Read More » -

Endpoint Protection Gartner Magic Quadrant July 2025
In today’s relentlessly dynamic digital world, organizations face a barrage of new challenges every day—from ever-expanding systems and a surge…
Read More » -
PCI SSC Releases Version 3.2 of the PCI Point-to-Point Encryption (P2PE) Standard
The PCI Security Standards Council (PCI SSC) has released version 3.2 of the PCI Point-to-Point Encryption (P2PE) Standard, introducing important…
Read More » -
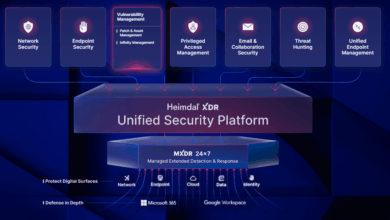
Attack Surface Management Software: Top 10 Vendors
Key Takeaways: What is attack surface management? Why is attack surface management important? What are the best ASM vendors? Over…
Read More » -
10 Digital Identity Examples for Small Business Owners
VikingCloud reports that one in five SMBs believe they’d be forced out of business if they fell prey to a…
Read More » -

The 4 CISM Domains Explained
The CISM® (Certified Information Security Manager®) qualification from ISACA® is one of the most widely respected credentials for information security…
Read More » -

Back to Business: Lumma Stealer Returns with Stealthier Methods
Conclusion The Lumma Stealer case exemplifies the adaptability and persistence of modern cybercriminal groups. Despite a major enforcement action, the…
Read More » -

PCI Secure Software Standard v2.0
From 10 July to 11 August, eligible PCI SSC stakeholders are invited to review and provide feedback on the…
Read More »