CAPTIX
-

Heimdal® Achieves Fifth Consecutive ISAE 3000 SOC 2 Type II Certification
COPENHAGEN, Denmark, July 23, 2025 – Heimdal is proud to announce that it has once again secured the ISAE 3000…
Read More » -
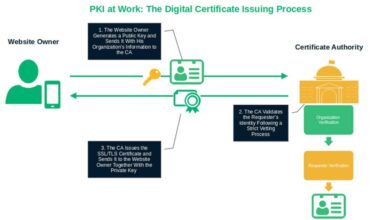
How Does PKI Work? A Look at the Inner Workings of Public Key Infrastructure
You enjoy the benefits of PKI every day, but have you ever wondered what goes on behind the scenes? Learn…
Read More » -
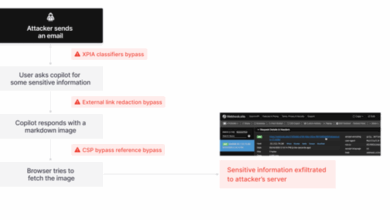
The New Reality of GenAI-Driven Attacks
Just a few years ago, several cybersecurity reports proclaimed that there was minimal evidence that bad actors were using generative…
Read More » -

The 4 CRISC Domains Explained
The CRISC® (Certified in Risk and Information Systems Control®) certification from ISACA® is a globally recognised credential for IT and…
Read More » -

Revisiting UNC3886 Tactics to Defend Against Present Risk
On July 18, Singapore’s Coordinating Minister for National Security K. Shanmugam revealed that the country was facing a highly sophisticated…
Read More » -
Don’t Miss These 2025 PCI SSC Community Meeting Agenda Highlights
We are excited to announce that the full agendas for the PCI SSC 2025 North America, Europe, and Asia-Pacific Community Meetings are…
Read More » -

Here’s how to spot and stop them
The conversational AI market is exploding. Grand View Research suggests it’s set to jump from $11.58 billion in 2024 to…
Read More » -
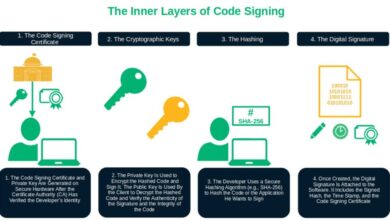
5 Real-World Software Nightmares That Code Integrity Verification Could Have Prevented
Learn from the past to prepare for the future with these 5 infamous cyber attacks (and their disastrous consequences) that…
Read More » -
U.S. CISA adds D-Link cameras and Network Video Recorder flaws to its Known Exploited Vulnerabilities catalog
U.S. CISA adds D-Link cameras and Network Video Recorder flaws to its Known Exploited Vulnerabilities catalog Pierluigi Paganini August 06,…
Read More » -

CISOs and Auditors Build Trust
Back in 1789, Benjamin Franklin wrote a letter to a French scientist named Jean-Baptiste Le Roy in which he penned…
Read More »