CAPTOL
-

What Is Social Engineering in Cybersecurity?
How many times have you heard the phrase “don’t trust strangers”? The key point today is that many strangers disguise…
Read More » -
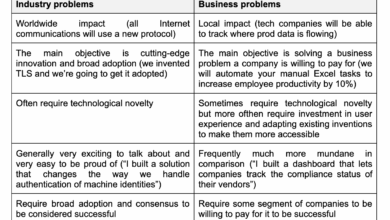
In security, not every industry problem is a business problem
Nobody can deny that there are many problems in our field. Just attend an industry conference or speak with five…
Read More » -

Cyber Security & Cloud Expo Europe welcomes a host of top industry experts to the speaker line-up!
Cyber Security & Cloud Expo Europe welcomes a host of top industry experts to the speaker line-up! Cyber Security &…
Read More » -

CIO Imperatives: Dr. Timothy C. Summers on Digital Trust, AI, and Why a Trusted CISO is Non-Negotiable 1
CIO Imperatives: Dr. Timothy C. Summers on Digital Trust, AI, and Why a Trusted CISO is Non-Negotiable In an era…
Read More » -

Black, White and Gray Box
Editor’s note: On the example of network security, Uladzislau describes the essence, pros and cons of black, gray, and white box…
Read More » -
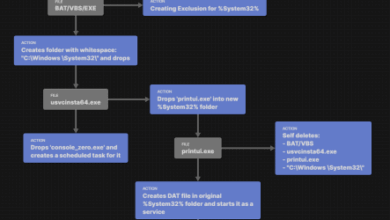
Hijacking Your Resources for Profit
Crypto Mining Crypto mining is the process by which individuals or organizations use computer power to solve complex mathematical problems,…
Read More » -

Back-to-school cyber safety: Parent checklist
Summer is flying by and before you know it, you’ll be buying backpacks and taking first-day-of-school photos. Back-to-school season brings…
Read More » -

Smart Home Data Breach Exposes 2.7 Billion Records
Mars Hydro, a Chinese company that makes IoT devices like LED lights and hydroponics equipment, recently suffered a massive data…
Read More » -

What Is a Data Breach and How to Prevent It?
Let’s be honest: few phrases can make your stomach drop faster than “your data has been compromised.” Whether you’re an…
Read More » -
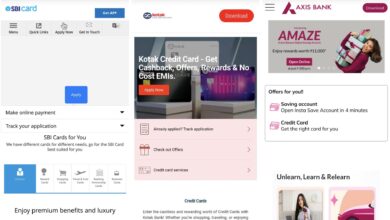
Android Malware Targets Indian Banking Users to Steal Financial Info and Mine Crypto
Authored by Dexter Shin McAfee’s Mobile Research Team discovered a new Android malware campaign targeting Hindi-speaking users, mainly in India.…
Read More »