CAPTUR
-

Not Every Task Deserves One
Hello CyberBuilders 🖖 This week, I’m diving into a brilliant video from Mr. Zhang at Anthropic. You might know him…
Read More » -

A Journey to the Highest Cybersecurity Maturity: Remediation, Part 5
Remediation Cycle Continue reading on The CISO Den »
Read More » -
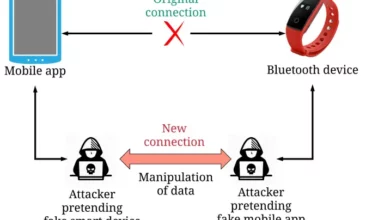
Bluetooth Vulnerability: Mitigating Risks Across Devices
I.Introduction Bluetooth has become an integral technology for billions of smartphones, computers, wearables, and other devices to connect and exchange…
Read More » -

When ‘Trust But Verify’ Isn’t Enough: Navigating AI-Driven Deception
The Threat That Knows What You Trust It sounds like your colleague. It looks like your CEO. It knows your…
Read More » -

What does a good password policy really look like? — Matt Palmer
Passwords should be the easiest area of security. Every organisation has a password policy. Every organisation used passwords. Everyone at…
Read More » -

What Agentic AI Can Fix in Cybersecurity
Cybersecurity is often perceived as being at a breaking point. The speed of business outpaces the tools and workflows meant…
Read More » -

The Immanence of the Useless. It is good that is not any good | by Vicente Aceituno Canal | Assorted Thoughts
It is good that is not any good Zoom image will be displayed Photo by Madalyn Cox on Unsplash “Perfection…
Read More » -
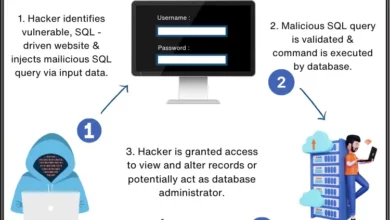
Defend Your Apps: SQL Injection Prevention Guide
Introduction In the era of digitalization, data security has become a paramount concern. Every day, countless businesses and organizations rely…
Read More » -

Why is Jersey introducing a new Cyber Security Law?
In 2021 I took a new role as Director of Jersey’s newly formed cyber response unit. We’ve come a long…
Read More » -
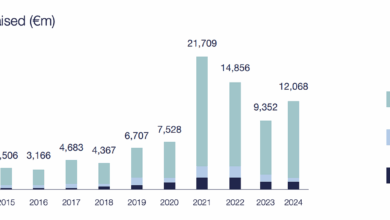
Fewer Cheques, Tougher Checks: Cyber VC in 2025
Hello Cyber Builders 🖖 Cybersecurity is at the top of everyone’s mind, and AI brings more opportunities and threats at…
Read More »