CAPTUR
-
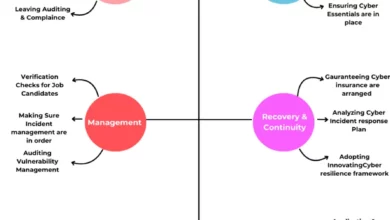
A CISO’s Take on Cyber Protection
Introduction In a rapidly evolving business landscape, cybersecurity is paramount amidst frequent cyber-attacks, emphasizing the crucial role of a Chief…
Read More » -

Training for Offense, Not Just Defense
Some topics in cybersecurity stir discomfort. Here’s one: what if your people weren’t just trained to detect risk, but to…
Read More » -

Introducing Guernsey Cyber Security Centre — Matt Palmer
Since 2021, I’ve been building Jersey Cyber Security Centre (JCSC). As a cyber defence capability for an island state and…
Read More » -

Breaking Down Credential Phishing Trends: How Can NDR Help?
Cybercriminals have changed tactics. Credential phishing has overtaken ransomware as the most common way to breach enterprise networks. What started…
Read More » -
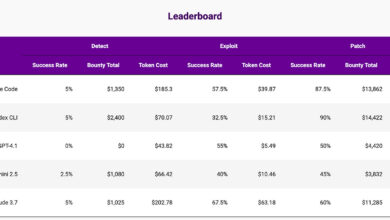
Application Security – AI Won’t Save You
Hello, Cyber‑Builders 🖖 Continuing our July series on application security, I want to discuss something that’s currently all over the…
Read More » -
Proactive MDR Strategies for Rapid Response
On July 18, 2025, a critical cybersecurity incident laid bare a zero-day vulnerability in Microsoft SharePoint Server. These were the…
Read More » -

CISO, how do you measure maturity? | by Vicente Aceituno Canal | The CISO Den
No, is not how you thought Zoom image will be displayed ISMS maturity is not a measurement of how good…
Read More » -

Securing Industry 4.0: Cybersecurity Challenges in Manufacturing and IoT
Introduction The manufacturing industry is rapidly evolving with Industry 4.0 technologies like IoT, Big data, AI, and automation enhancing production…
Read More » -

when you don’t respond to a crisis — Matt Palmer
A few years ago I wrote a short article about the Titanic, and the lessons for cyber risk management. However,…
Read More » -

The Link Between Asset Classification and Threat Response Accuracy
The cybersecurity landscape continues to evolve at an unprecedented pace, with organizations facing increasingly sophisticated threats targeting their most valuable…
Read More »