CAPVEX
-
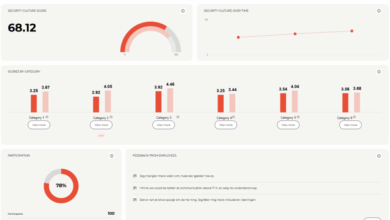
Measure, Compare, and Improve Your Security Culture
Your organisation’s security culture plays a huge role in how well you can defend against phishing attacks and data breaches.…
Read More » -

A Script to Query for EC2 Instance Type by Memory, VCPUs, and Cost | by Teri Radichel | Cloud Security | Jun, 2025
Using Amazon Q helped write the script in < 3 hours (2 if you don’t count the security rabbit hole)…
Read More » -

Look out for phony verification pages spreading malware
Before rushing to prove that you’re not a robot, be wary of deceptive human verification pages as an increasingly popular…
Read More » -

Maximizing Rewards and Token Benefits
Integrating WeatherXM Stations with FrysCrypto: A Dual Mining Guide Note: This article does not consist of any endorsement of either…
Read More » -

The Biggest GDPR Fines of 2024 and Previous Years
Although companies have been adapting to the GDPR for years now, the enforcement of GDPR violations is still relatively new…
Read More » -

Amazon Q For Code to Deploy a User and Secret With Password | by Teri Radichel | Cloud Security | Jun, 2025
WARNING: Do not blindly create IAM resources with AI ~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~ ⚙️ Security Automation (Pre-AI). The Code. ⚙️ AI Automation. The…
Read More » -

Weekly Update 460
This week's update is the last remote one for a while as we wind up more than a month of…
Read More » -

An all-you-can-eat buffet for threat actors
ESET Research has been monitoring attacks involving the recently discovered ToolShell zero-day vulnerabilities 24 Jul 2025 • , 5 min.…
Read More » -
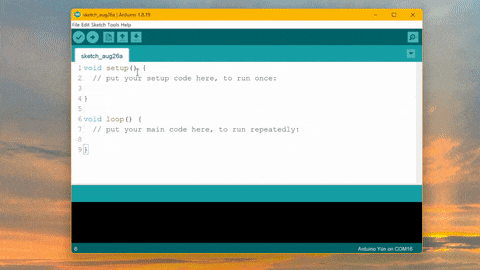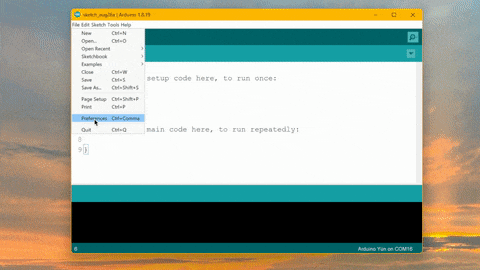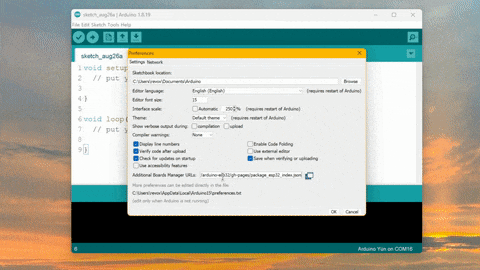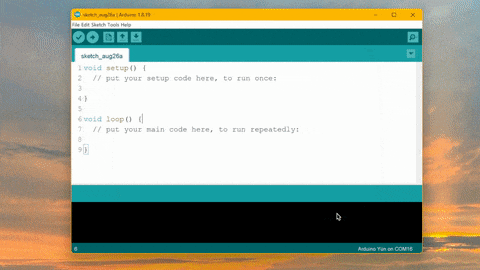
A Comprehensive Guide for Efficient Cryptocurrency Mining
How to Mine Duinocoin on ESP32 Have you ever wondered how to mine Duinocoin on your ESP32 device efficiently? In…
Read More » -
Use Built-In Phishing Reporting in Outlook or Gmail
The Current Reality: Chaos in Reporting Does the following sound familiar? Teams message: “Hey, I just got an email that…
Read More »