CAPVEX
-

Using 2nd Sight Lab’s aws-deploy to Deploy Any AWS Resource | by Teri Radichel | Cloud Security | Jul, 2025
Steps to deploy all the things — and summary of how I used AI ~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~ ⚙️ Security Automation (Pre-AI). The…
Read More » -

ToolShell attacks hit organizations worldwide
The ToolShell bugs are being exploited by cybercriminals and APT groups alike, with the US on the receiving end of…
Read More » -
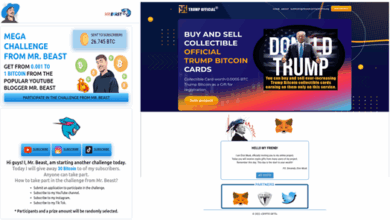
Researchers Expose Infrastructure Behind Cybercrime Network VexTrio
Researchers at Infoblox have released new findings on VexTrio, a large criminal enterprise that uses a set of traffic distribution…
Read More » -

What the data from +200.000 phishing emails learns us
Do you learn anything from sending thousands of phishing emails? YES, you do, and we want to share it with…
Read More » -

Using AI to Write Deterministic Code | by Teri Radichel | Cloud Security | Jul, 2025
Avoid blanket statements — use the right tool for the job ~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~ ⚙️ Security Automation (Pre-AI). The Code. ⚙️ AI…
Read More » -

Weekly Update 461
The Stripe situation is frustrating: by mandating an email address on all invoices, we're providing a channel that sends customer…
Read More » -

The hidden risks of browser extensions – and how to avoid them
Not all browser add-ons are handy helpers – some may contain far more than you have bargained for 29 Jul…
Read More » -

Maximize Connectivity with USB Standards & Ports Guide
USB standards and ports play a crucial role in connecting various devices to a computer or other electronic devices. Understanding…
Read More » -
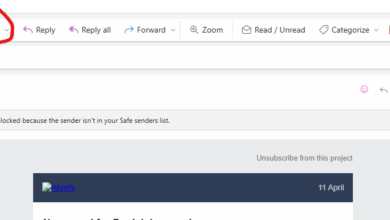
How our new phishing report button integrates directly with Microsoft Defender
Our newest phishing training feature takes simulation insights to a whole new level. CyberPilot is one of the first providers…
Read More » -

Ubuntu Snake Oil Certificate. About those “widely publicized… | by Teri Radichel | Cloud Security | Jul, 2025
About those “widely publicized instructions” in AI responses and consider the use of AWS ACM instead ~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~ ⚙️ Security Automation…
Read More »